If you missed, part I of this series is here.
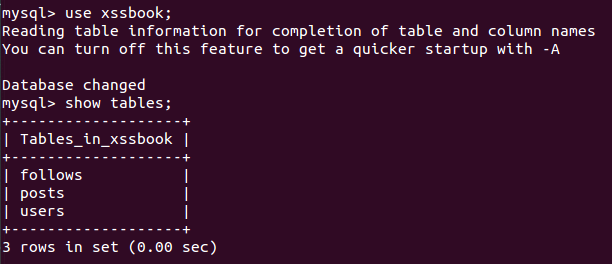
In order to understand our XSS worm in action, we will first see its spreading environment, a very simple social network. XSSbook, as we will call it, is basically the product of a database with just 3 tables:
Let’s see what we have into each one.
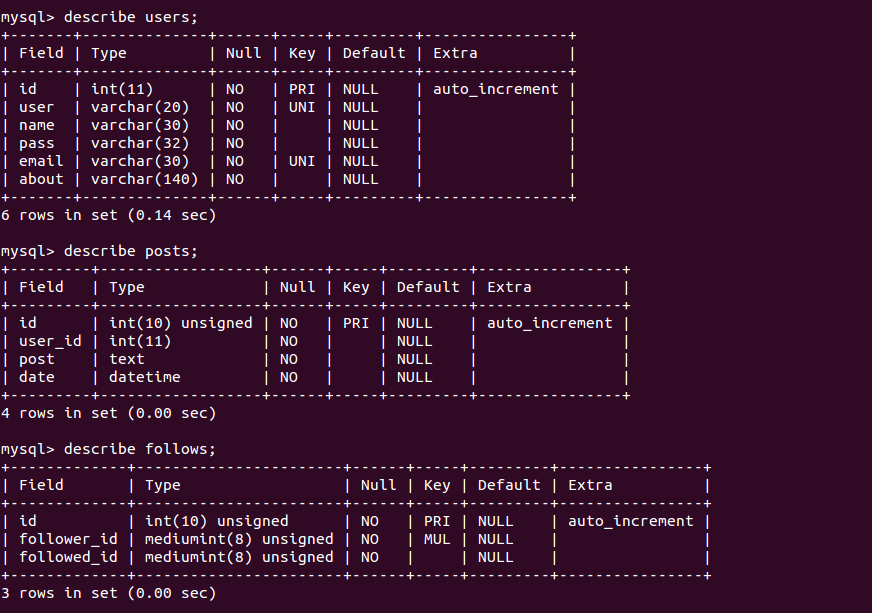
Table “users” has the profile of users of the system, with their identification number (id), user to login (user), their name (name), password in MD5 format (pass), email (email) and a field to talk shortly about themselves (about).
Table “posts” stores their posts with date and time, using their ids in the user_id field.
Lastly, table “follows” keeps the relationship between users by means of their ids to define who is following who: in the context of application this means which posts will appear in user’s timeline.
For the interface, a set of PHP scripts to handle the session, user input and database queries on each feature are enough to make this work.
The greatest challenge now is how to populate the database with fake data as closer as possible to a real world social network. For this, we will make use of bash scripts to generate data files to import into XSSbook. We will also try to follow the power law to reflect what happens with thousands of users connections.
In the next post we will see our XSS worm spreading across this populated database.


[…] by /u/Ne0xxx [link] […]
[…] If you missed, part I of this series is here. In order to understand our XSS worm in action, we will first see its spreading environment, a very simple social network. […]
[…] Be sure you have read parts I here and II here. […]
[…] The Genesis of an XSS Worm – Part II […]