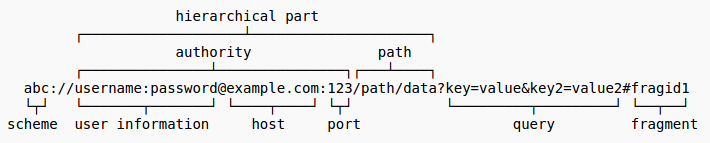
In the beginning of an URL lies an underlooked place useful to hide things from server logs. It’s the authentication part of the authority section. Check the full URL scheme below.
Differently from the fragment part, where we can use document properties like location.hash to store things that will never be sent to server, the user information will be sent but will not figure in logs for security reasons.
So it becomes another good place to put javascript code:
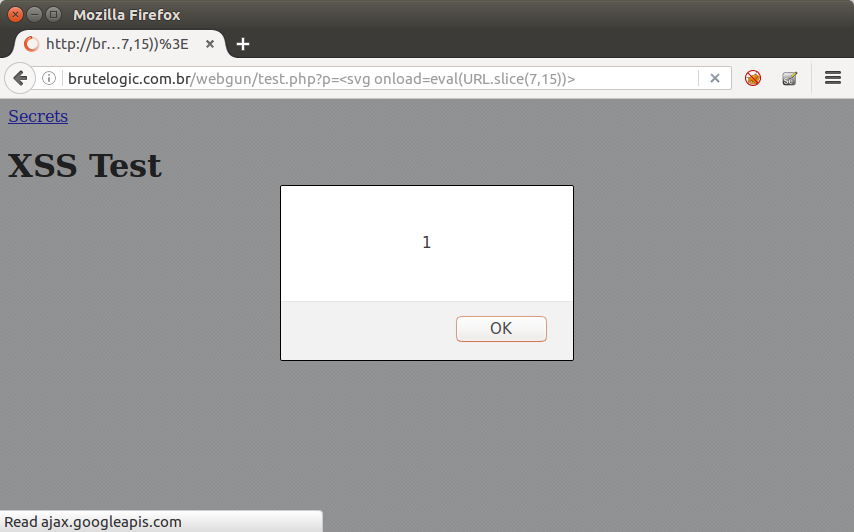
http://alert(1)@45.55.59.13/webgun/test.php?p=<svg+onload=eval(URL.slice(7,15))>
Using an slice of the string returned by window.URL property, starting from char 7 to char 15, we pass to eval() the string we want to execute. For a https enabled website, the right combination would be 8 and 16, respectively.
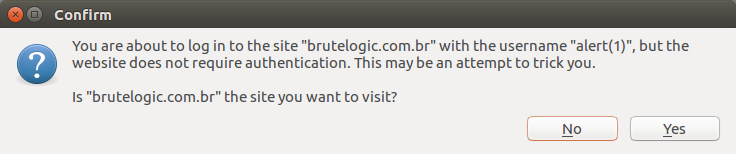
Although there’s a security warning in Firefox (but not in Chrome), the statement about the domain to visit (brutelogic.com.br) may lead user to a wrong conclusion.
After it, there will be no trace of what really happened in browser address bar.
The same can be done with the location property of document if eval() is not available.
http://javascript:alert(1)@45.55.59.13/webgun/test.php?p=<svg+onload=location=URL.slice(7,26)>
But much more harmful is to use this ability to actually do some kind of authentication. Because the victim of a XSS attack can perform requests to internal IP addresses, it’s possible to pivot to devices accessible only to the victim.
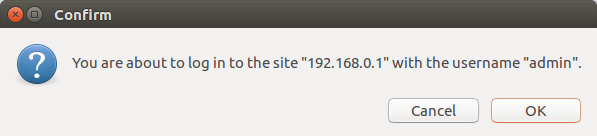
Most SOHO (Small Office / Home Office) routers are usually vulnerable to login attacks over this channel, so all an attacker has to do is to guess the right one in a small list of common default credentials. After, he/she proceeds with a basic CSRF attack to add his own DNS server to router configuration achieving total control over the victim’s network. But latest Firefox (version 48) is smart enough to stop automation and warn the user about it.
The same can’t be said about latest Chrome (version 52). It has no security warning again.
Click here to test your own router (Firefox or Chrome). If after clicking on “click me” your router dashboard appears, you may be in serious trouble.
#hack2learn